Lock It Down: The Critical Role of Ongoing Website Security and Maintenance
Your website is live, collecting user data, processing transactions, and representing your brand around the clock. But that polished digital presence is also a target. Without consistent upkeep, it can become a serious security risk, leaving you vulnerable to hacks, data breaches, and downtime. Website maintenance and security monitoring aren’t just best practices—they’re essential. Whether you're a grassroots nonprofit, a busy university, or a global enterprise, staying secure and up to date should be a top priority. Here's why it matters.
Why Website Security Maintenance Can’t Wait
Think of your website as a fortress: sturdy walls, watchful guards, and an ever-vigilant moat. But those guards need coffee breaks, the moat needs upkeep, and the walls can crack over time. Website maintenance is the blacksmith’s hammer, patching holes and sharpening iron. Here’s why skipping routines is like leaving the drawbridge down:
- Hackers Never Sleep: New vulnerabilities appear daily. A plugin that’s secure today can become a zero-day exploit tomorrow.
- Data Protection is Non-Negotiable: User trust hinges on keeping personal data safe. A single breach can tarnish your reputation forever.
- Compliance Matters: From GDPR to HIPAA to PCI DSS, regulatory requirements demand regular audits and security benchmarks. Failure to comply can lead to hefty fines.
- Performance & Credibility: A hacked or broken site erodes user trust. If your donation form or application portal gets compromised, users will bail—and they might never return.
Regularly scheduled checks—your “website security audit”—and ongoing website maintenance aren’t nice-to-haves; they’re lifelines.
The Anatomy of a Rock-Solid Maintenance Plan
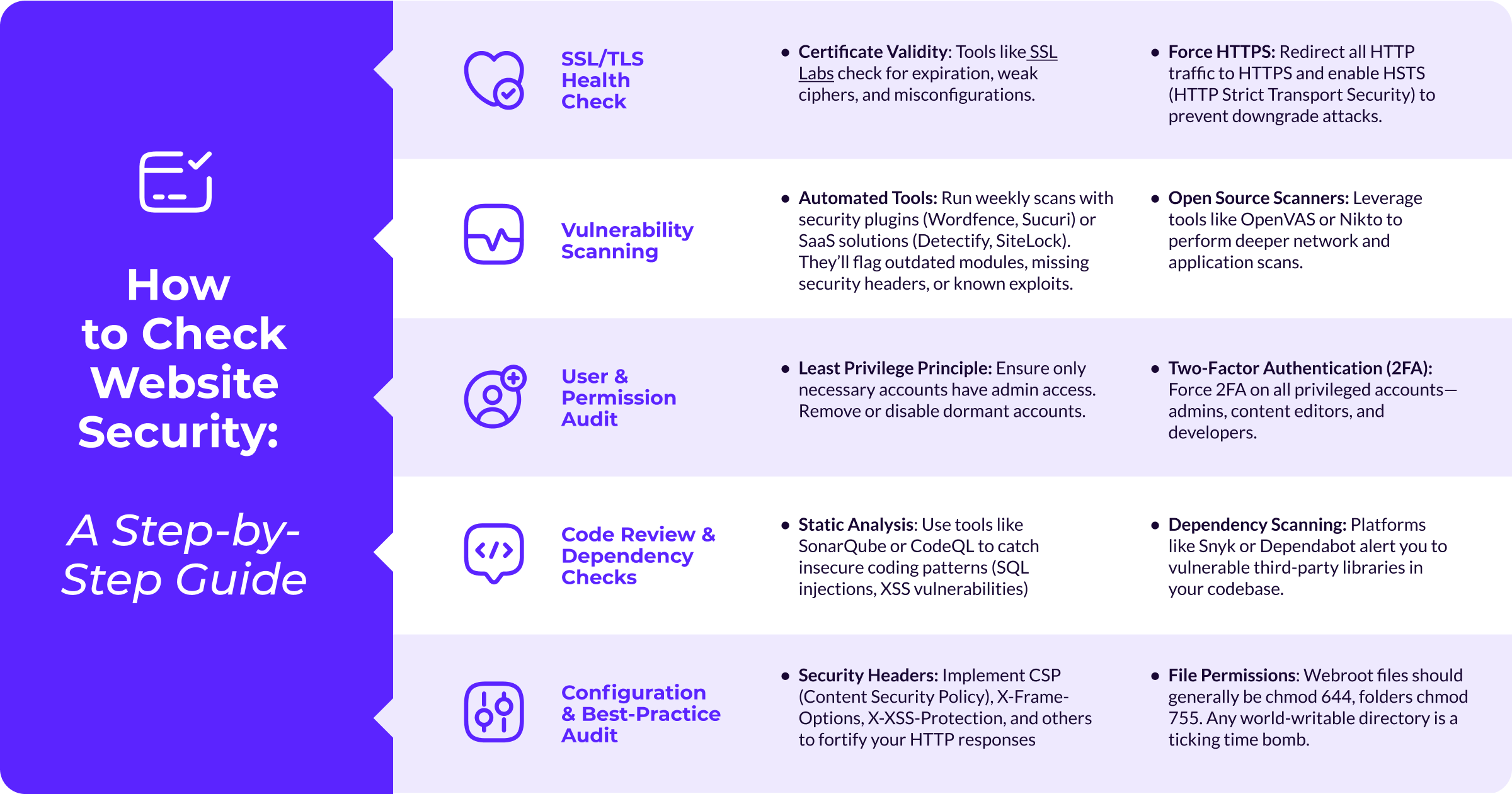
1. Frequent Security Audits & Vulnerability Scans
- Automated Scanning Tools: Use platforms like Sucuri or Qualys to run weekly scans for malware, outdated libraries, or weak configurations.
- Manual Penetration Testing (Pen Testing): At least annually, bring in an ethical hacker to simulate real-world attacks. They’ll uncover gaps that automated tools might miss.
- Checklists & Baselines: Maintain a website maintenance checklist that includes “permission checks,” “SSL certificate validity,” and “third-party script reviews.”
2. Patch, Update, Repeat
- Core & Plugin Updates: Whether you’re on WordPress, Drupal, or a custom CMS, apply security patches as soon as they’re released. Falling behind is an open invitation for attackers.
- Server-Side Hardening: Keep your OS (Linux, Windows Server) and webserver (Apache, Nginx) fully patched. Disable unused services and ports.
- Dependency Management: If your site uses Node.js, Python, or Ruby modules, ensure libraries don’t contain known vulnerabilities.
3. Ongoing Monitoring & Alerts
- Intrusion Detection Systems (IDS): Tools like OSSEC or Wazuh can detect suspicious file changes or unusual login patterns in real time.
- Log Analysis: Aggregate logs (SSH, Apache/Nginx, database) into a centralized SIEM (e.g., Splunk, ELK Stack). Set up alerts for repeated failed logins, SQL errors, or unauthorized file modifications.
- Uptime & Performance Monitoring: Services like Pingdom, Uptrends, or Datadog watch your site’s availability and response times. If your homepage goes dark or slows to a crawl, you’ll know instantly.
4. Regular Backups & Disaster Recovery
- Automated Backups: Schedule daily or hourly backups of your database, codebase, and file storage. Store them offsite—in AWS S3, Azure Blob, or a secure FTP server.
- Recovery Drills: Every quarter, simulate a full restore to verify backups work and your DR process is smooth. If restoring takes 24+ hours, it’s time to streamline.
5. Continuous Security Education & Policy Updates
- Internal Training: Ensure your team knows how to spot phishing attempts, maintain strong passwords, and follow least-privilege principles.
- Documentation & Runbooks: Keep a living document detailing “how to revoke a compromised API key,” “how to rotate certificates,” and “how to close security holes in legacy code.”
Putting It All Together: A Maintenance & Security Workflow
1. Daily
- Check automated backup logs.
- Monitor uptime/response alerts.
- Review intrusion detection alerts if configured.
2. Weekly
- Run vulnerability scanner and review results.
- Patch any critical OS, CMS core, or plugin updates.
- Review web server logs for suspicious activity.
3. Monthly
- Perform a full security audit against your website maintenance checklist.
- Verify backups by doing a restore test.
- Check SSL/TLS configurations and renew certificates as needed.
- Review user accounts and permissions.
4. Quarterly
- Conduct pen testing or hire an external security consultant.
- Update security policy and train key stakeholders on emerging threats.
- Audit third-party integrations and remove any deprecated or unused scripts.
5. Annually
- Review disaster recovery plan and run a tabletop exercise.
- Renew domain registrations, service contracts, and security certificates.
- Perform a comprehensive compliance audit (e.g., GDPR, HIPAA, PCI DSS).
Ongoing Maintenance 101
All this security talk ties directly to our core thesis: Ongoing website maintenance is the anchor that prevents costly mistakes—downtime, data breaches, SEO penalties. If you haven’t walked through our quick guide, Why Your Drupal Website Needs Ongoing Maintenance: Avoiding Costly Mistakes, now’s the perfect time. It lays out a complete maintenance checklist—from module updates to performance tuning—that dovetails with the security practices above.
Final Thoughts: Don’t Wait for Disaster
A breach or major outage isn’t just an inconvenience; it’s a brand wound that can take years to heal. Ongoing website security maintenance is about more than “keeping the lights on”—it’s about building bulletproof trust with your audience. By auditing, patching, monitoring, and educating, you transform your site from a sitting duck into a digital fortress.
Ready to lock down your site and ensure uninterrupted service? Establish a proactive maintenance routine today—because the only acceptable breach is the one you never had. Get in touch with our maintenance and security team to get started.